HTTP vs SOCKS5 Proxy: What are the Differences & Benefits?

Have you ever wondered how your device communicates with the internet or…

Have you ever wondered how your device communicates with the internet or…

With the advancement in technology and as more services go online, people…

🔥 My go-to VPN: 60% Off Special Been using VPNBaron as my…

Anipy-cli is a versatile Python tool that allows you to watch and…

Setting up Rclone on a remote server to connect to Google Drive…

In the world of WordPress, the use of themes and plugins is…
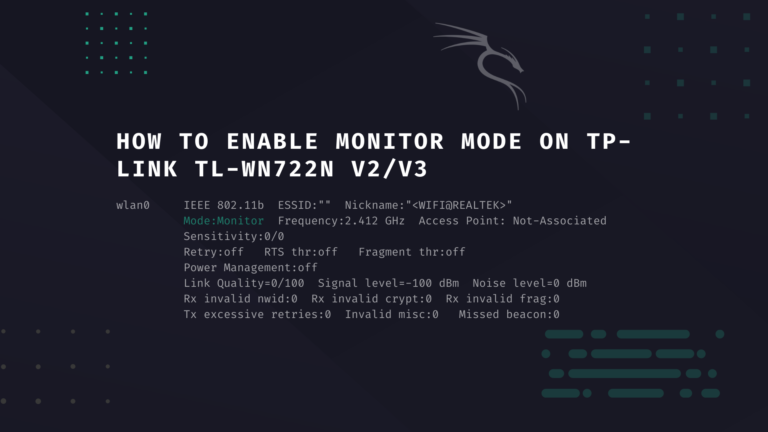
In this tutorial we’ll enable monitor mode on a TP-LINK TL-WN722N V2/V3…

Metasploit, one of the most widely used penetration testing tools, is a…

If you are just getting started with penetration testing and ethical hacking,…

Anybody who wants to get started with Ethical hacking or wants to…

This post will explain SQL injection, the impact of successful SQL attacks,…
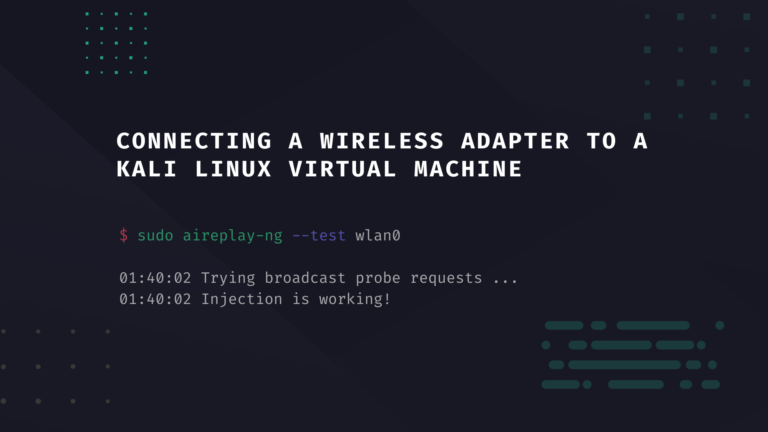
In “Network hacking,” most people get confused when talking about Network adapters…